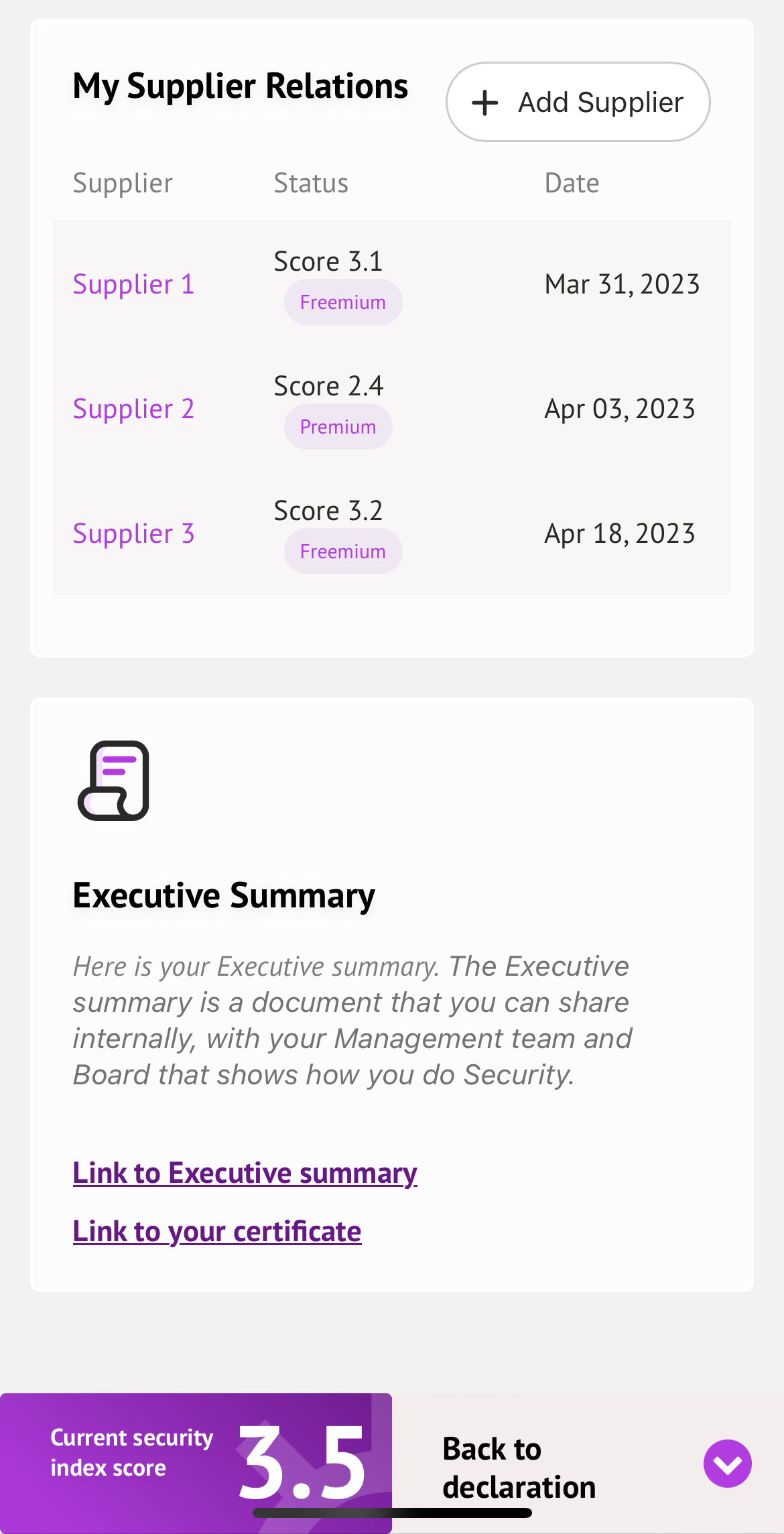
Essential entities
Energy – Electricity, heating and cooling, Oil, Gas, Hydrogen
Transport – Air, Train, Water, Road
Bank – Credit institution, Financial market and infrastructure
Healthcare - healthcare providers, medical products, pharmaceuticals, medical equipment
Drinking water & Waste water
Digital infrastructure – Data centers, cloud providers, electronic communications
Public sector – National and regional authorities
Space